
Space Cloud provides robust and flexible mechanisms to secure your apps/services at both layers:
Application layer security consists of two parts:
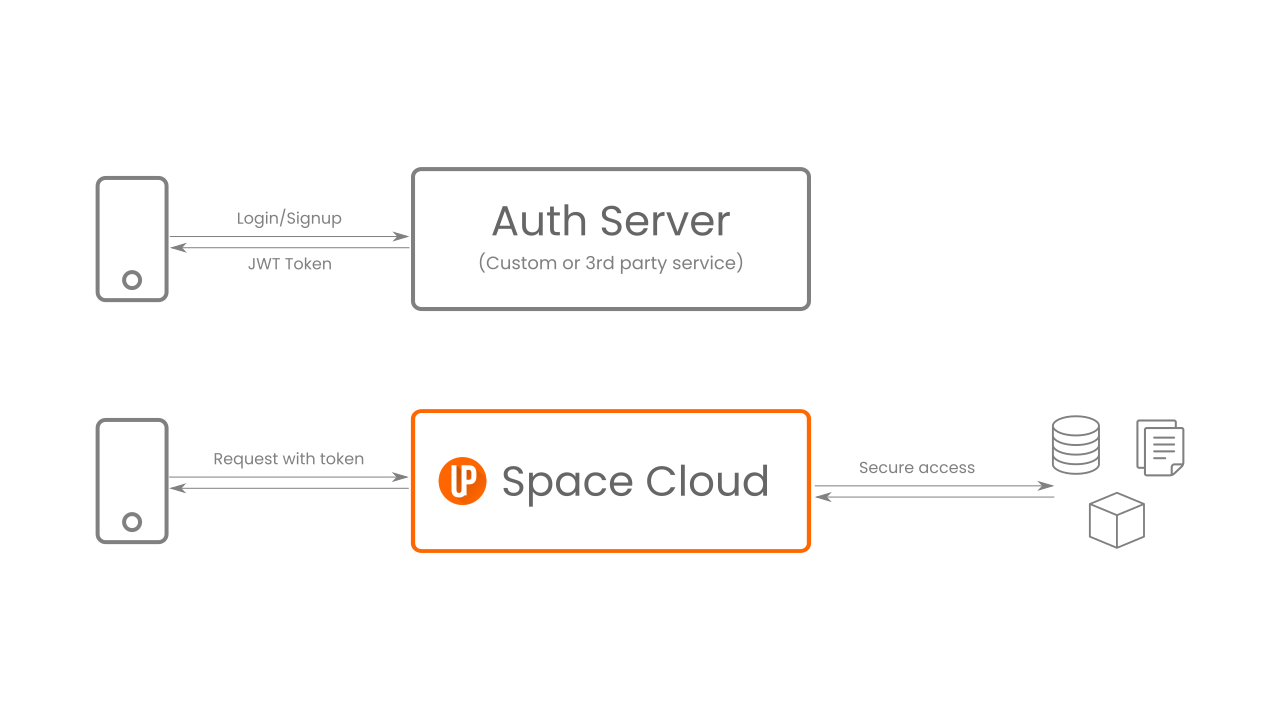
As you can see, authentication is performed outside of Space Cloud. However, it validates whether a request is authenticated and enforces your authorization/access-control logic. Space Cloud only expects a JWT token in each of your incoming requests. You can read more about using JWTs with Space Cloud from here.
As a developer, you need to write security rules via Space Cloud’s admin console. All incoming requests to the Space Cloud are first validated by Space Cloud’s API controller using the security rules defined by you.
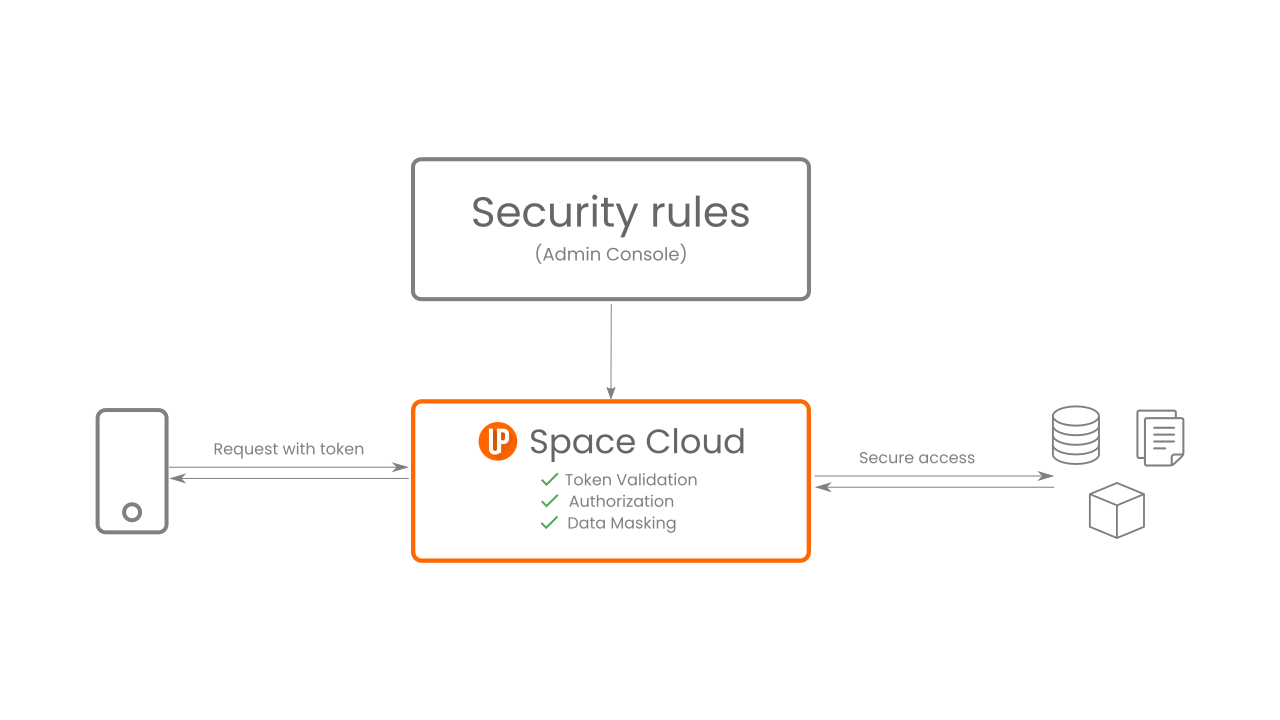
Security rules help check whether a request is authenticated and authorized. It can even modify the request/response before passing it on to the next stage. A request is allowed to be made, only if the security rules for that resource are resolved.
Here’s an example of a simple security rule for granting access to a resource only if the user’s role is admin:
{
"rule": "match",
"type": "string",
"eval": "==",
"f1": "args.auth.role", // assuming JWT consist of a claim named role
"f2": "admin"
}
Security rules help you perform various access control operations like:
On the platform layer, Space Cloud utilizes the power of Kubernetes and Istio under the hood to provide you with the following security benefits: